Download the sample application callerInfo from the Oracle Website http://www.oracle.com/technology/sample_code/tech/java/codesnippet/security/jaznldap/JAZNLDAP.zip.
Install Oracle Access Manager components.
Install an Oracle Application Server for example 10.1.3.1 (Oracle HTTP Server 1.x/Apache 1.3.x)
Install WebGate 10.1.4.2 BP03 (THIS IS VERY IMPORTANT, there are some important bug fixes in BP03 WebGate see metalink note: 736372.1 for version / patchsets)
Install AccessGate 10.1.4.2 BP06 (THIS IS VERY IMPORTANT, there are some important bug fixes in BP06 AccessGate see metalink note: 736372.1 for version / patchsets)
Create an OC4J container and deploy the callerInfo.ear file.
Create users en groups in the OID:
http://www.oracle.com/technology/sample_code/tech/java/codesnippet/security/jaznldap/UsingDAS.html
1. Configure Oracle Access Manager
1. Configure Oracle Access Manager Form-Based Authentication
2. Configure Oracle Access Manager Basic Authentication
3. Configure the Resource Type
4. Protect the Action URL
1.1 Configure Oracle Access Manager Form-Based Authentication
For Single Sign-On functionality, a form-based authentication scheme must protect the resources.
1.1.1 Create a Login Form
The login form can be a very simple HTML page with an FORM in the page
- The action of the form can be an bogus link (in this example /oam/access/test.html) but this must be the same as in the authentication scheme which is created later on.
- The userid and password can be chosen freely but these will also be used in the authentication sheme.
login1.html
<HTML>
<HEAD>
</HEAD>
<body>
<center>
<h1>User Login</h1>
<br>
<br>
<form name="myForm" action="/oam/access/test.html" method="post">
Username: <input type="text" name="userid" width="20"><br />
Password: <input type="password" name="password" width="20"><br />
<input type="submit" value="OK">
</form>
</body>
<html>
This login1.html file can be placed in $ORACLE_HOME/Apache/Apache/htdocs/public.
1.1.2 Define Form-Based Authentication in Policy Manager
Go to the Access Manager GUI: http://hostname:port/access/oblix and click the Access System Console link, login with the administrator account.
Access System Console > Access System Configuration > Authentication Management
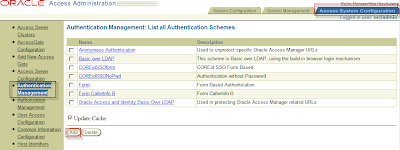
Click button Add to create an Form Based Authentication.
Fill in the entries like this:
(pay attention:
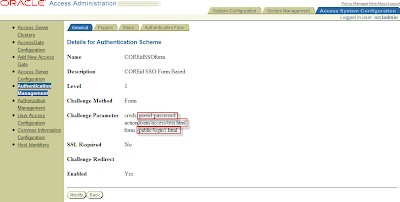
Name: COREidSSOform (choose freely)
Description: COREid SSO Form Based (choose freely)
Level: 1
Challenge Method: Form
Challenge Parameter: form: /public/login1.html (see the location in step 1.1.1)
creds: userid password (use the same variable names as in the login1.html in step 1.1.1)
action: /oam/access/test.html (use the same action as in the login1.html in step 1.1.1)
passthrough: No
SSL Required: No
Challenge Redirect Enabled: Yes
1.1.3 Configure the credential_mapping Plug-In for Form-Based Authentication
Now you have to configure the credential_mapping plugin_in for form-based authentication.
Click on tab plugin and click the button add.
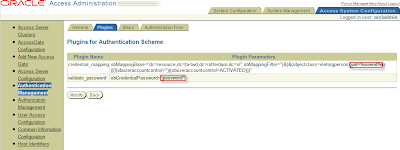
First configure the credential_mapping (this is important, if password is the first plugin it will not work) select the plugin in the drop down box.
For Plugin Parameters:
obMappingBase="cn=users,dc=us,dc=oracle,dc=com",obMappingFilter="(&(&
(objectclass=inetorgperson)(uid=%userid%))(|(!
(obuseraccountcontrol=*)) (obuseraccountcontrol=ACTIVATED)))"
The value for uid must match the variable specified for user name in the login1.html form and in the creds part of the Form Based Authentication.
This also corresponds to the value of the coreid.name.attribute option in the Oracle Access Manager login module configuration in OC4J.
1.1.4 Configure the validate_password Plug-In for Form-Based Authentication
Now configure the validate_password plug-in select validate_password in the drop down box.
The Plugin Parameters:
obCredentialPassword="password"
The value for obCredentialPassword must match the variable specified for password in the login1.html form and in the creds part of the Form Based Authentication.
This also corresponds to the value of the coreid.password.attribute option in the Oracle Access Manager login module configuration.
1.1.5 Create Host Identifier
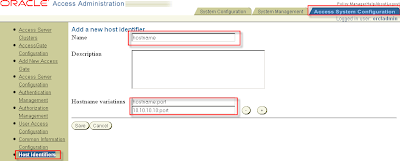
Access System Configuration > Host Identifiers
Click Add
Name: Hostname
Description: (Choose freely)
Hostname variations: hostname:port
ip address:port
1.2 Configure Oracle Access Manager Basic Authentication
You must configure the Oracle Access Manager basic authentication scheme, which must not be password protected (only credential_mapping plug-in). This scheme will protect two resources
- A URL assouciated with resource type (myresourcetype). The Oracle Access Manager
login module will use this URL to communicate to the Access Server through the
Access Manager SDK.
- The Action URL in the login1.html (/oam/access/test.html) page. This is so submitted form requests can be
intercepted by WebGate in order to enforce rules for submitted credentials.
However the application itself must be protected by form-based authentication (steps 1.1.1 and 1.1.2)
1.2.1 Define Basic Authentication in Policy Manager
Go to the Access Manager GUI: http://hostname:port/access/oblix and click the Access System Console link, login with the administrator account.
Access System Console > Access System Configuration > Authentication Management

Click button Add to create Basic Authentication.
Fill in the entries like this:
(pay attention:
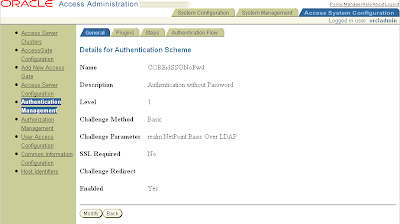
Name: COREidSSONoPwd (choose freely)
Description: Authentication without Password (choose freely)
Level: 1
Challenge Method: Basic
Challenge Parameter: realm:NetPoint Basic Over LDAP
SSL Required: No
Challenge Redirect
Enabled: Yes
1.2.2 Configure the credential_mapping Plug-In for Basic Authentication
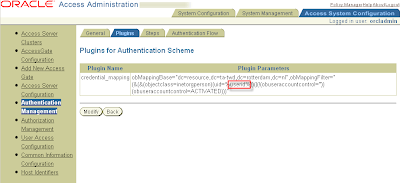
Now you have to configure the credential_mapping plugin_in for form-based authentication.
Click on tab plugin and click the button add.
First configure the credential_mapping (this is important, if password is the first plugin it will not work) select the plugin in the drop down box.
For Plugin Parameters:
obMappingBase="cn=users,dc=us,dc=oracle,dc=com",obMappingFilter="(&(&
(objectclass=inetorgperson)(uid=%userid%))(|(!
(obuseraccountcontrol=*)) (obuseraccountcontrol=ACTIVATED)))"
The value for uid must match the variable specified for user name in the login1.html form and in the creds part of the Form Based Authentication.
This also corresponds to the value of the coreid.name.attribute option in the Oracle Access Manager login module configuration.
1.3 Configure the Resource Type
In Oracle Access Manager, a resource type describes the kind of resource to be protected, including its associated operations. Operations associated with a resource are tied to its type. You must configure an Oracle Access Manager resource type for your resource, and then protect your resource type, action URL, and application.
The Oracle Access Manager login module will need information for the resource type, as will be noted. OC4J uses the resource type to retrieve user information based on the Oracle Access Manager ObSSOCookie or the user name, using APIs of the Access Manager SDK.
1.3.1 Configure the Name and Operation of the Resource Type
Access System Console > Access System Configuration > Common Information Configuration > Resource Type Definitions
On the page that lists all resource types, choose to add a new resource type.
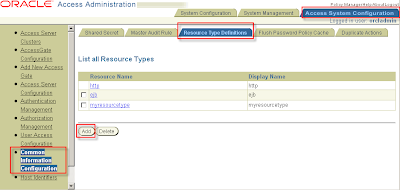
Make entries such as the following to define a new resource type:
Resource Name: myresourcetype (choose freely)
Display Name: myresourcetype (choose freely)
Resource Matching: Case Insensitive
Resource Operation: MYRESOURCEOPERATRION (choose freely)
You can choose any names for the resource type and resource operation, but you must use the same names for the coreid.resource.type and coreid.resource.operation option values in the Oracle Access Manager login module configuration.
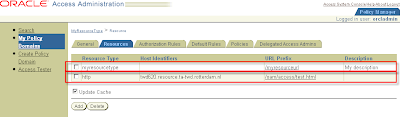
1.3.2 Configure and Protect the URL of the Configured Resource Type
After authentication, OC4J requires access to the user's roles in order to check for authorization. To enable this, you must set up an Oracle Access Manager "return action" that allows Oracle Access Manager to return the appropriate roles to OC4J for the user after successful authentication.
To set up the return action in Oracle Access Manager, navigate as follows:
Policy Manager > Create Policy Domain
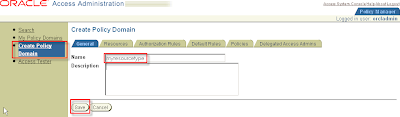
Policy Manager > My Policy Domains > myresourcetype > tab Resources
Create Resource for myresource type
Click button Add
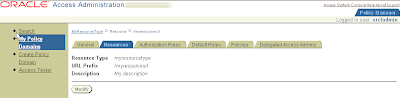
Resource Type: myresourcetype (step 3.1)
Host Identifiers: hostname (step 1.5)
URL Prefix: /myresourceurl (choose freely)
Description: (choose freely)
Button Save
The URL prefix must start with a "/" and is the designated URL of the resource type. This must match the value of the coreid.resource.name option in the Oracle Access Manager login module configuration.
1.3.3 Configure the Return Action Attributes
After authentication, OC4J requires access to the user's roles in order to check for authorization. To enable this, you must set up an Oracle Access Manager "return action" that allows Oracle Access Manager to return the appropriate roles to OC4J for the user after successful authentication.
To set up the return action in Oracle Access Manager, navigate as follows:
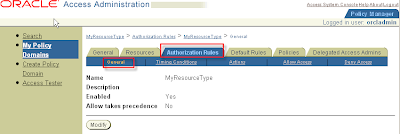
Policy Manager > My Policy Domains > MyResourceType > Authorization Rules tab
Click button Add
Name: MyResourceType (choose freely)
Description (choose freely)
Enabled Yes
Allow takes precedence No
Click button Save
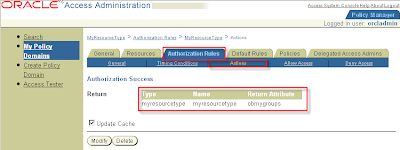
Under the Authorization Success tab section, add the following entries (continuing the preceding example using myresourcetype):
Return Type: myresourcetype
Return Name: myresourcetype
Return Attribute: ObMyGroups
1.4 Protect the Action URL
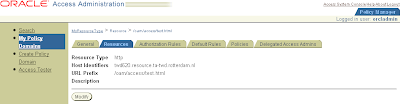
Create Resource for http type action url (/oam/access/test.html)
Policy Manager > My Policy Domains > myresourcetype > tab Resources
Create Resource for myresource type
Click button Add
Resource Type http
Host Identifiers hostname (step 1.5)
URL Prefix /oam/access/test.html action URL in login1.html
Description (choose freely)
IMPORTANT:
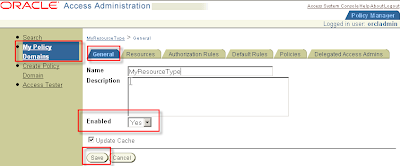
Do not forget to enable the policy:
My Policy Domains > MyResourceType > General
Click modify
Set Enable to Yes and click save.
Overview:
2. Configure OC4J with the Access Manager SDK
After that the SDK is installed the SDK needs be registered against the Access Server and the already installed WebGate. Pay attention the order of configuring is important. First the Access Server then the WebGate.
Configure SDK against Access Server:
Go to the directory
cd SDK_HOME/AccessServerSDK/oblix/tools/configureAccessGate
./configureAccessGate -i /SDK_HOME/AccessServerSDK/ -t AccessGate -w NAME_WEBGATE -m open -S -P PASSWORD -h ACCESS_SERVER_HOSTNAME -p ACCESS_SERVER_PORT -a ACCESS_SERVER_NAME
Output:
Preparing to connect to Access Server. Please wait.
AccessGate installed Successfully.
Configure SDK against WebGate:
./configureAccessGate -i /SDK_HOME/AccessServerSDK/ -t AccessGate -w SDK_NAME -m open -S -P PASSWORD -h HOSTNAME_WEBGATE -p ACCESS_SERVER_PORT -a ACCESS_SERVER_NAMEOutput:
Preparing to connect to Access Server. Please wait.
AccessGate installed Successfully.
2.1 Configure the Access Manager SDK to Each OC4J Instance
You will need Oracle Access Manager SDK, one installation for each OC4J instance, on the same system as OC4J. The Access Manager SDK is required by OC4J at runtime to communicate with Access Server. OC4J must be given the Access Manager SDK location during startup (through the java.library.path property), so that it can initialize the SDK. Note this initialization occurs only if at least one application is using Oracle Access Manager as the security provider.
2.1.1 Copy jobaccess
Copy the Oracle Access Manager file jobaccess.jar from the Access Manager SDK to the OC4J path. You will find this file in the SDK_HOME/AccessServerSDK/oblix/lib directory. Create the directory ORACLE_HOME/j2ee/home/lib/ext (if it does not already exist) and copy the jobaccess.jar to that directory.
2.2 Configure the Access Manager SDK Library Path for Each OC4J Instance
Configuring opmn.xml for Oracle Access Manager
Where OC4J is managed by OPMN, add settings to opmn.xml for Oracle HTTP Server and OC4J, as follows, when you use Oracle Access Manager:
1. Set the LD_ASSUME_KERNEL environment variable to the value "2.4.19".
2. Set the LD_LIBRARY_PATH environment variable to point to the AccessServerSDK library path.
3. Add the AccessServerSDK library path to java.library.path as a start parameter.
Then restart the OC4J instances.
Following is an opmn.xml example for the OC4J home instance. Repeat these settings for the OC4J_SOA instance and any other OC4J instances as appropriate:
<ias-component id="OC4J">
<process-type id="oc4j_callerinfo" module-id="OC4J" status="enabled">
<environment>
<variable id="LD_ASSUME_KERNEL" value="2.4.19"/>
<variable id="LD_LIBRARY_PATH"
value="/SDK_HOME/AccessServerSDK/oblix/lib" append="true"/>
</environment>
<module-data>
<category id="start-parameters">
<data id="java-options" value="-server ...
-Djava.library.path=/SDK_HOME/AccessServerSDK/oblix/lib
... />
</category>
...
</module-data>
...
</process-type>
...
</ias-component>
3. Configure the CallerInfo Application
3.1 Protect the Application URL's in web.xml
The first step in protecting your application is to protect appropriate URLs or URL prefixes through settings in the web.xml file, using standard J2EE features.
These are the same URLs that you will you protect through Oracle Access Manager.
And add the following code:
<login-config>
<auth-method>BASIC</auth-method>
</login-config>
3.2 Settings for Application Deployment
In Oracle Application Server 10.1.3.x implementations, Application Server Control does not yet support Oracle Access Manager as a security provider. When you deploy your application using the Application Server Control Console, choose the file-based provider. This will be overridden through the configuration steps documented in this blog.
3.3 Configure Oracle Access Manager SSO in orion-application.xml
To use Oracle Access Manager Single Sign-On as the authentication method for Web applications, set the auth-method attribute to "COREIDSSO" in the
<jazn provider="XML" default-realm="jazn.com" jaas-mode="doAsPrivileged">
<jazn-web-app auth-method="COREIDSSO"/>
</jazn>
You also need to add the mapping between de application role and the OID group:
<!-- mapping for realm "jazn.com" -->
<security-role-mapping name="sr_manager">
<group name="managers" />
</security-role-mapping>
<security-role-mapping name="sr_developer">
<group name="developers" />
</security-role-mapping>
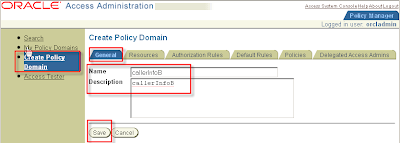
3.4 Protect the Application URL's in Oracle Access Manager
Policy Manager > Create Policy Domain
Name : callerInfoB
Description: callerInfoB
Click button save
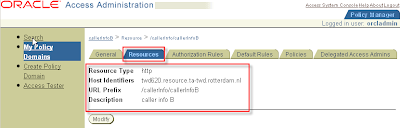
Tab Resources
Resource Type http
Host Identifiers hostname
URL Prefix /callerInfo/callerInfoB
Description caller info B (choose freely)
Click button Save
Tab Authorisation Rules > SubTab General
Name Everyone (choose freely)
Description Everyone (choose freely)
Enabled Yes
Allow takes precedence No
Click Save
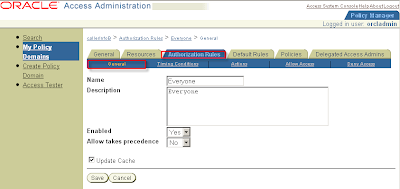
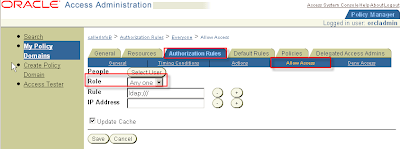
Tab Authorisation Rules > SubTab Allow Access
Role Any one
Click Save
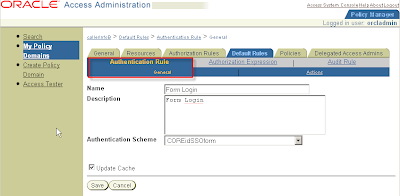
Tab Default Rules > SubTab Authentication Rule > SubSubTab General
Name: Form Login
Description: Form Login
Authentication Scheme: COREidSSOform
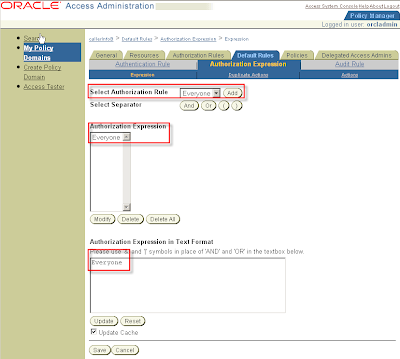
Tab Default Rules > SubTab Authorization Expression > SubSubTab Expression
Select Authorization Rule: Everyone
Click button Add > Click button Save
IMPORTANT:
Do not forget to enable the policy:
My Policy Domains > CallerInfoB > General
Click modify
Set Enable to Yes and click save.
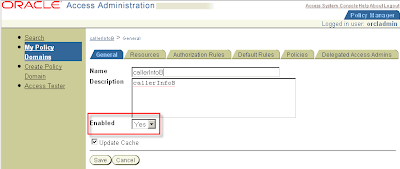
3.5 Configure the Oracle Access Manager Login Module
For a Web application, the OC4J implementation to support Oracle Access Manager requires the login module CoreIDLoginModule, supplied by Oracle. The following template shows the general form of the configuration, in the system-jazn-data.xml file.
$ORACLE_HOME/j2ee/CONTAINER_NAME/config/system-jazn-data.xml
<application>
<name>callerinfo</name>
<login-modules>
<login-module>
<class>oracle.security.jazn.login.module.coreid.CoreIDLoginModule</class>
<control-flag>required</control-flag>
<options>
<option>
<name>coreid.password.attribute</name>
<value>password</value>
</option>
<option>
<name>coreid.name.attribute</name>
<value>userid</value>
</option>
<option>
<name>addAllRoles</name>
<value>true</value>
</option>
<option>
<name>coreid.resource.operation</name>
<value>MYRESOURCEOPERATION</value>
</option>
<option>
<name>coreid.resource.type</name>
<value>myresourcetype</value>
</option>
<option>
<name>coreid.resource.name</name>
<value>/myresourceurl</value>
</option>
</options>
</login-module>
</login-modules>
</application>
3.6 Test the application
WebGate will intercept this request and will check the authentication scheme for this URL. The configuration shown earlier in this chapter will result in the user being prompted with the login.html login form from "Create a Login Form". Then the following sequence will take place:
1. WebGate will capture the user name and password from the login form and communicate to Access Server.
2. Access Server will communicate to Oracle Internet Directory (or other LDAP repository that you use).
3. After the user is authenticated, the Oracle Access Manager SSO token will be returned to WebGate.
4. WebGate will set the ObSSOCookie and pass the cookie and other HTTP headers to mod_oc4j, which will route the request to the appropriate OC4J instance.
5. OC4J will take the cookie and validate it, or retrieve roles for the user associated with this cookie from Access Server using the Access Manager SDK configured on OC4J.
http://hostname:port/callerInfo
Application:
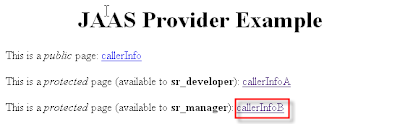
Click on the link for managers: callerInfoB
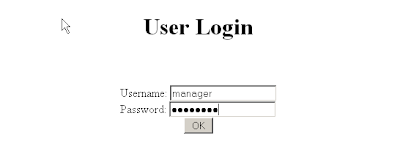
Login screen (login1.html):
Login as manager/password
Application shows roles:
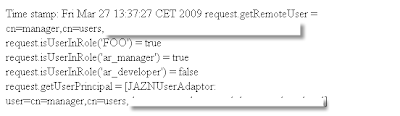
Refers:
http://download.oracle.com/docs/cd/B31017_01/web.1013/b28957/coreid.htm#BJEBJCCF
Did this post help you in any way can you please leave a comment? This will motivate me writing more posts.


![Validate my Atom 1.0 feed [Valid Atom 1.0]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiwsk0jkCpg60orkOvHQLaU5Kfnb72Q4Fv59o0rzOSTRknWzbGrBmh31ZjGOZdIt4C_wLVtBkWfFwG5eMfJQQ1E7MlTWYYZhWtFG6ndJemCWSu5DypAo_UP6u1Y20xCR_N-ksYP5OzvrUkE/s400/valid-atom.png)



Very,Very, Very nice - Sean Davis
ReplyDeleteThank you so much. It is very informative and useful. We followed it and could successfully integrate the application with OAM.
ReplyDeleteIs there a way , getRemoteUser can return only the username instead of the full DN?.
Thanks
HK
Hi HK,
ReplyDeleteI do not know if there is a way to return only the username. I am not a programmer.
Kind regards,
Arjan
Hi Arjan,
ReplyDeleteI asked that question because , only when we integrate with OAM(CoreIDLoginModue), we get the full DN.
Otherwise, with file based or LDAP based or OSSO , we just get the username in a call to getRemoteUser.
So, I was thinking it might be some setting/configuration parameter in OAM.
Thanks
HK
HI
ReplyDeleteI have given in the same way for form based authentication but i am getting an error.
what ever password i am giving it is accepting any password its accepting could you help me.
Thanks
Regulla
Top Post!
ReplyDeleteBedankt!
Willem
hi,
ReplyDeletecan you provide your inputs on writing a custom access gate. i need to protect a resource which is running on a application server say jboss.
thanks
Hi,
ReplyDeleteNo, I can not help you with that, maybe you can log an SR at metalink.
Regards,
Arjan
Hello Arjan,
ReplyDeleteI configured Form Based AuthN... When I access the protected appln. It shows the for to enter the login creds and after providing the creds it re-routes to /access/dummy and not to the protected page. I have used /access/dummy.cgi as the Form action.
any help would be greatly appreciated.
Regards,
Ferry
Is the action of the form protected by the access system?
ReplyDeleteUse the Access tester to see.
Otherwise protect /access/dummy.cgi with an Access system policy or enable the default policy (if you chose to configure Policies during install).
Yes I have protected the /access/dummy.cgi with policy using Basic AuthN scheme.
ReplyDeleteAny idea on how to debug this situation ???
ReplyDeleteone question: When I protect the /access/dummy url.. wht r the mandatory parameters we should enter in the policy.
ReplyDeleteHello.. an update... when unauthzd users access the protected page, he is authnticated and oam shows the error stating he is not authrzd.
ReplyDeleteHowever, when authzd user logins to the form..he gets the form displayed again... any help would be appreciated.
Thanks for this article - I got this working in minutes on a test setup.
ReplyDeleteHI Arjan,
ReplyDeleteNice post!
Could you please confirm if we need to add any custom resource type for this implementation? Or existing http resource type would do?
Also, will this solution work for BPEL worklist application deployed in OC4J container? I want to achieve SSO for BPEL worklist using OAM.
So, can I achieve this with webgate or should I implement custom access gate ? Please confirm.
THanks,
Mahendra.
Very cool blog! question.. on the Tab for Authorisation Rules > SubTab Allow Access
ReplyDeleteCould you descrive how to write a Rule?
I am trying to allow only members of a certain group in AD access a resource.
example (only members of the "toy" group can access the toy website.